Ransomware Revil Kaseya
Kaseya still hasnt released a patch for the vulnerability that REvil used to spread ransomware to as many as 1500 companies. Making matters worse some of Kaseyas customers involved in.

Revil Ransomware Attack On Kaseya What To Know And What To Do Threat Education Webinar Youtube
Reports indicate that the REvil gangs supply chain attack exploited the.

Ransomware revil kaseya. Kaseya says the REvil supply-chain ransomware attack breached the systems of roughly 60 of its direct customers using the companys VSA on. Updated Kaseya ransomware attack FAQ. Playbook includes the following tasks.
Firm Kaseya dated July 2 2021 has been attacked by a supply chain attack conducted by a Russian hacker group REVILThe Kaseya VSA IT. This ransomware was most famously used in the recent Kaseya and colonial pipeline ransomware attacks. REvil is also known as Ransomware Evil.
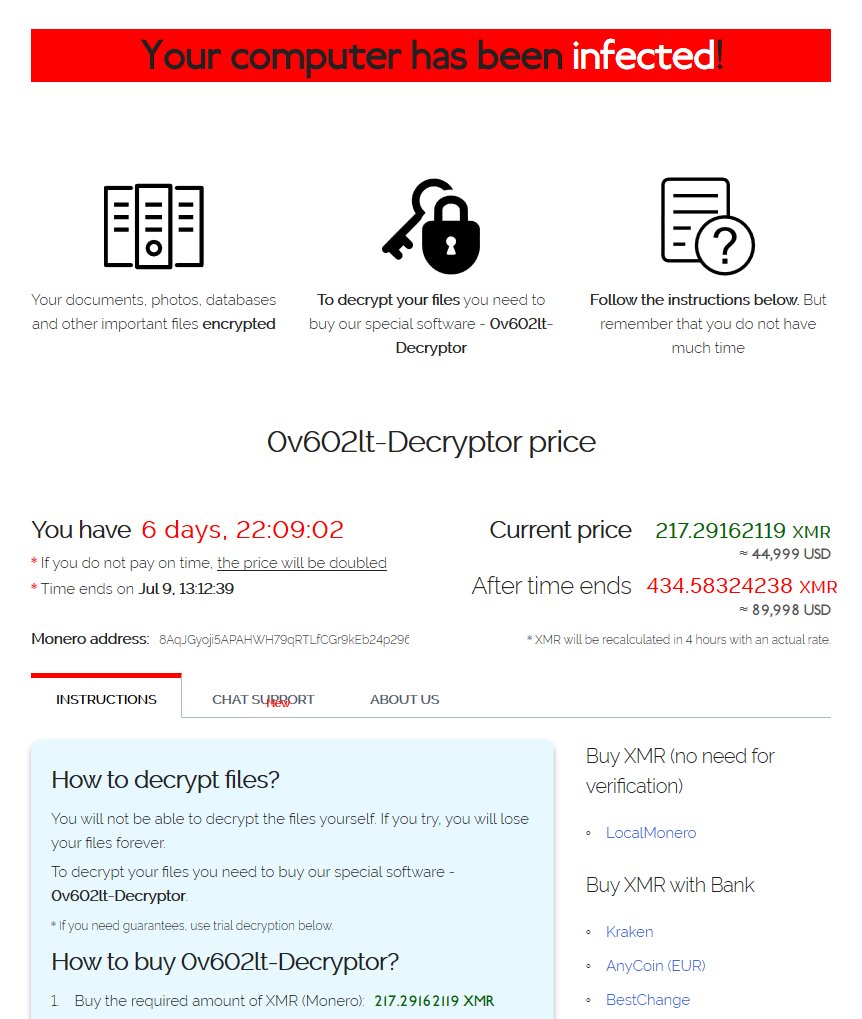
Just ahead of the July 4th holiday weekend a ransomware attack targeted organizations using Kaseya VSA remote management softwareThe outfit behind the attack REvil initially requested a 70 million ransom and claimed to have locked down millions of devices. Kaseya were hit through powerful ransomware attack in opposition to its VSA product. It offers universal decryptor to affected systems.
Kaseya VSA is a popular piece of software for remote network management used by many managed security providers or MSPs companies that provide IT. In July the REvil ransomware gang attacked dozens of managed service providers MSAs exploiting a zero-day authentication vulnerability in the Kaseya VSA remote management tool. Managed Service Provider platform Kaseya has shut down its cloud servers and warned customers after a malicious software update delivered REvil ransomware to.
Attack chain of Kaseya VSA Ransomware attack. Kaseya VSA administrative access was disabled to the compromised servers and the notorious REvil aka Sodinokibi ransomware was delivered to other machines in their networks. On July 2nd the REvil ransomware operation launched a massive.
It is most co. Collect related known IOCs from several sources. An analysis of the malicious software by the cybersecurity firm Emsisoft shows that it was created by REvil.
Kaseya VSA is an automated software patch management and vulnerability management system. The Kaseya attack is being called one of the largest ransomware attacks in history. Kaseya received a universal decryptor that allows victims of the July 2nd REvil ransomware attack to recover their files for free.
Kaseya VSA 0-day - REvil Ransomware Supply Chain Attack playbook. That was before REvil suddenly went offline on July 13th disconnecting its servers abandoning forums and shutting down a page on. Is a fake management agent update Beaumont commented.
What we know now. Services at many companies was compromised by these attackers shipping ransomware to all the endpoint companies. The ransomware group makes use of software updates through the Kaseya VSA agent hotfix and delivers the REvil.
As a result attackers encrypted 60 MSAs along with 1500 other companies. Indicators PS commands Registry changes and known HTTP requests hunting using PAN-OS Cortex XDR and SIEM products. As a spate of ransomware attacks continue to dominate the headlines in recent months the infamous REvil ransomware gang has upped the ante significantly with a wide ranging operation that is suspected to have impacted thousands of small-to-midsize businesses through the compromise of a leading IT services provider.
The massive ransomware attack compromised up to 1500 businesses. To be clear this. This management agent update is actually REvil ransomware.
Kaseya the software firm whose remote access tool was used to deliver REvil ransomware to hundreds of businesses around the world this month in a devastating supply-chain attack has obtained a. Management software commonly used by managed service providers who work IT. Experts said it was absolutely possible for REvil to have created separate decryption keys for each victim but the ransomware group eventually came forward to offer Kaseya.
This malicious hotfix contained a ransomware payload called Sodinokibi known to be released by a notorious group called REvil which resulted in the encryption of the server and shared folders. Hit by a severe cyberattack earlier this month IT enterprise firm Kaseya said on Thursday that it obtained a universal decryptor key for recent victims of the REvil ransomwareKaseya.

Kaseya Sera What Revil Shall Encrypt Shall Encrypt Splunk

Kaseya Supply Chain Attack Targeting Msps To Deliver Revil Ransomware Truesec Blog

Kaseya Patches Vsa Vulnerabilities Used In Revil Ransomware Attack

Kaseya Supply Chain Attack Targeting Msps To Deliver Revil Ransomware Truesec Blog
Kaseya Supply Chain Ransomware Attack Hits Msp Customers Security Itnews

Kaseya Ksa Supply Chain Attack Sees Revil Ransomware Sent To 1 000 Companies

Revil Ransomware Attack At 200 Companies Via Kaseya Vsa And Management Service Provider Msp Born S Tech And Windows World
Devastating Revil Ransomware Attack Is Potentially One Of The Biggest Hacks So Far

The Kaseya Vsa Revil Ransomware Supply Chain Attack How It Happened How It Could Have Been Avoided Security Boulevard

Revil Sodinokibi Ransomware Delivered Through Kaseya Vsa Supply Chain Attack Emanuele De Lucia

Revil Ransomware Attack On Kaseya Demanding 70m For Decryption Keys Askcybersecurity Com

Revil Ransomware Gang Executes Supply Chain Attack Via Malicious Kaseya Update The Record By Recorded Future

The Kaseya Company Has A Decryptor For The Revil Ransomware
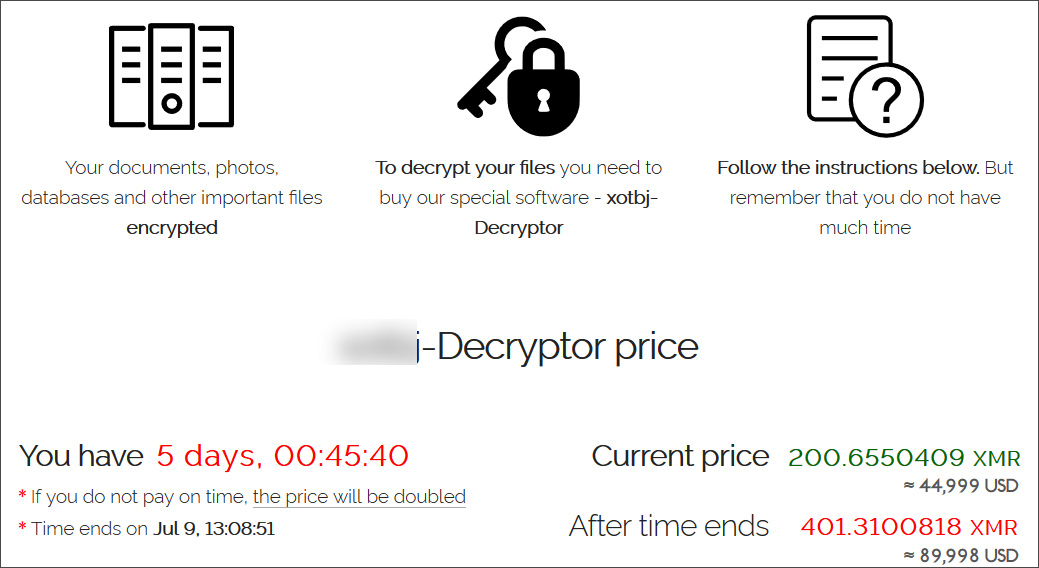
Revil Is Increasing Ransoms For Victims Of The Kaseya Ransomware Attack News Block

Kaseya Ransomware Attack Sets Off Race To Hack Service Providers Researchers Reuters
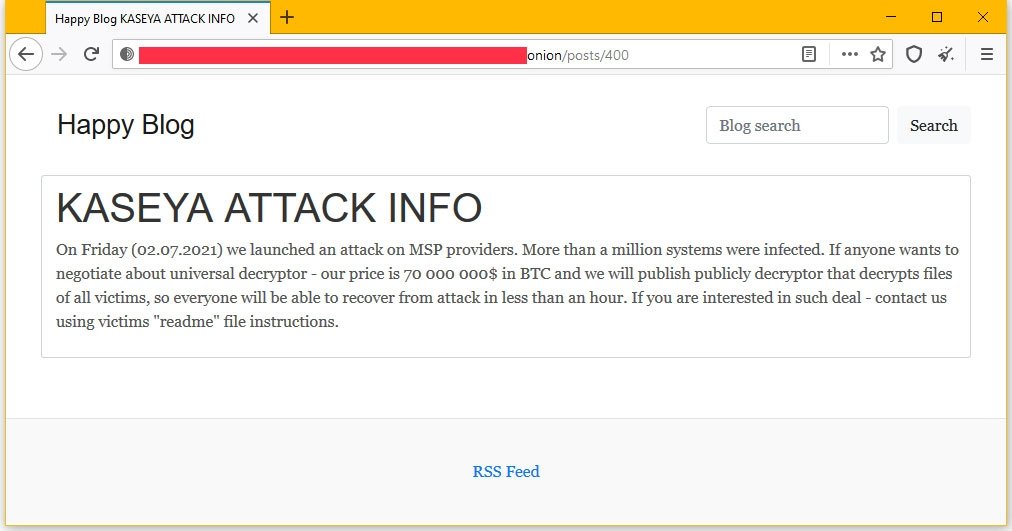
Revil Demands 70m To End Kaseya Ransomware Attack Appleinsider
/cdn.vox-cdn.com/uploads/chorus_asset/file/8792129/acastro_170621_1777_0008.jpg)
19 Days After Revil S Ransomware Attack On Kaseya Vsa Systems There S A Fix The Verge

The Kaseya Revil Attack Explained Bugcrowd

Revil Ransomware Deployed In Kaseya Supply Chain Attack Soc Prime