Ransomware Revil / Sodinokibi
Kaseya a company that provides IT management software to managed service providers MSPs and IT companies has been hit with a REvil aka Sodinokibi ransomware attack at the dawn of the Fourth of July weekend as reported in the companys own announcement. REvil is highly configurable and shares code similarities with the GandCrab RaaS.
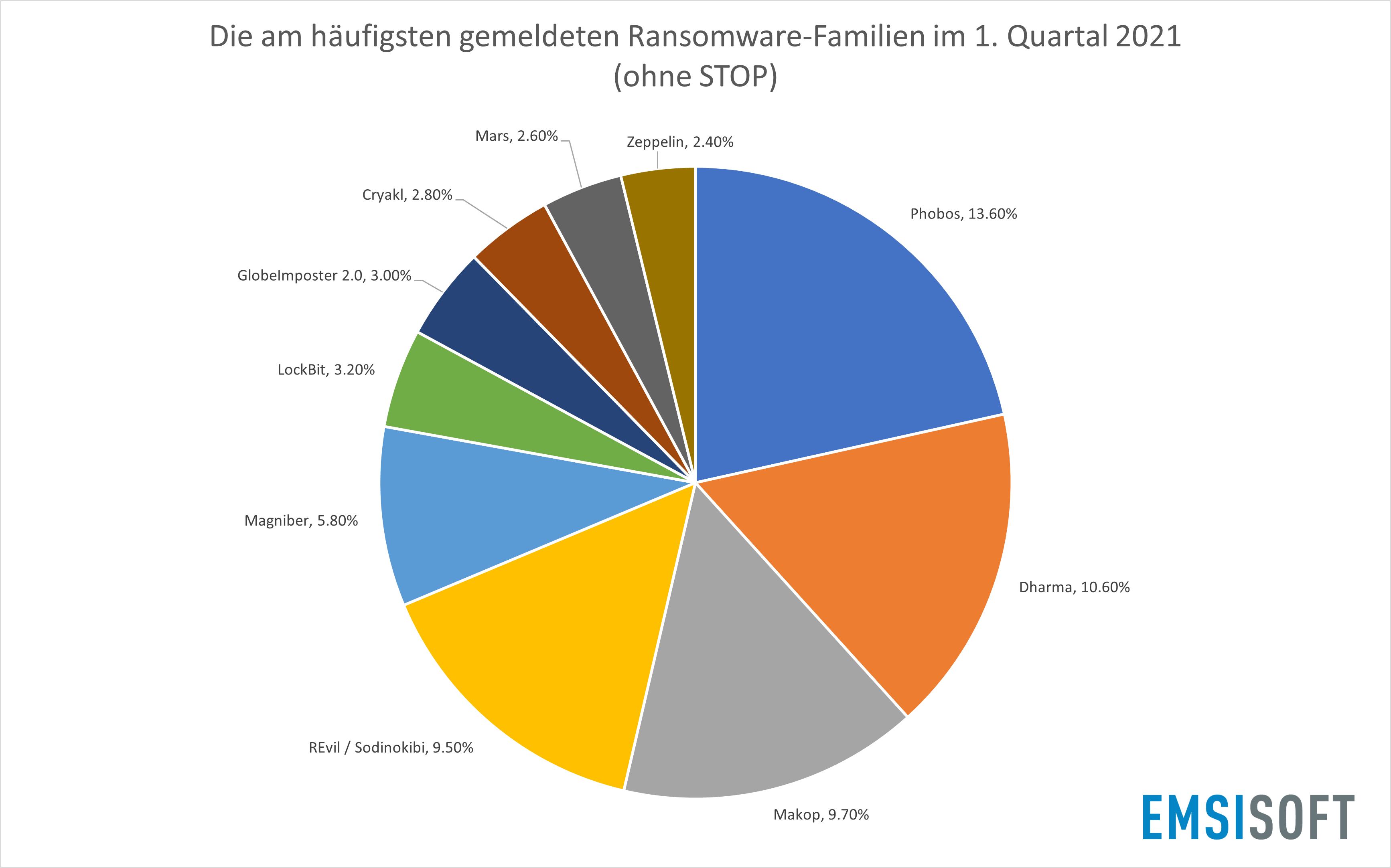
Statistikbericht Zu Ransomware 1 Quartal 2021 Emsisoft Sicherheitsblog
Advanced Ransomware which makes system changes and encrypts files.

Ransomware revil / sodinokibi. SODINOKIBI REVIL RANSOMWARE SUMMARY. REvil auch bekannt als Sodinokibi ist ein ausgereiftes und weit verbreitetes Ransomware-as-a-Service RaaS Angebot. Around this same time the GandCrab ransomware crew announced they would shut down their operations.
We examine three major ransomware families that employ these schemes. The prevalent threat is known to wipe backup files encrypt files on local shares and exfiltrate data. Kriminelle Kunden können die Ransomware von den Entwicklern leasen und mit eigenen Parametern versehen auf den Computern ihrer Opfer platzieren.
Notably all three also operate under a ransomware-as-a-service RaaS scheme which means that they are propagated more. Sodinokibi or REvil was first discovered in April of 2019 where it was seen exploiting a vulnerability in Oracle WebLogic. Sodinokibi is distributed with a Ransomware-as-a-Service business model allowing anybody who can pay can become an operator of the virus.
Sodinokibi REvil Threat Summary Sodinokibi REvil Evolution and Attacks Remove Sodinokibi Ransomware Sodinokibi is the name of a new ransomware which is currently being distributed in aggressive campaigns. If you are one of them this article will provide you with more details about Sodinokibi ransomware. REvilSodinokibi is highly evasive and takes many measures to prevent its detection by antivirus and other means.
REvil is one of the most prominent providers of ransomware as a service RaaS. Mittlerweile zeigen sich viele Sicherheitssoftware-Hersteller und unabhängige IT-Security-Experten überzeugt davon dass REvil auch bekannt als Sodinokibi. Here are some of the interesting insights Per the operators it meant Ransom.
We handpicked these three since they are currently active feature new techniques target big companies and perform different levels of extortion. The authors of REvilSodinokibi have previously been connected to the same authors of the prolific GandCrab ransomware which was recently retired. Sodinokibi Entwickler leaken Daten.
An uncensored interview between the Russian OSINT and REvil operator has popped up in one of the hacking forums today. Sodinokibi is one of the most lucrative ransomware strains of 2020 with its creators cyber-criminal gang REvil recently claiming over 100 million in profits this year alone. GandCrab is responsible for 40 of all ransomware infections globally.
It shares many similarities to the GandCrab ransomware strain that retired around the same time Sodinokibi popped up leading researchers to speculate whether this ransomware is operated by the same people. The typical attack vector chosen by this group is either the exploitation of vulnerable network devices or brute-force attacks on Remote Desktop Protocol servers. McAfees Advanced Threat Research team ATR observed a new ransomware family in the wild dubbed Sodinokibi or REvil at the end of April 2019.
One of the ransomware-as-a-service RaaS we encounter most frequently known alternately as Sodinokibi or REvil is as conventional a ransomware as weve seen. It is used by the financially motivated GOLD SOUTHFIELD threat group which distributes ransomware via exploit kits scan-and-exploit techniques RDP servers and backdoored software installers. During a recent client engagement the LIFARS DFIR team encountered the REvil Sodinokibi Ransomware group.
This criminal group provides adaptable encryptors and decryptors infrastructure and services for negotiation communications and a leak site for publishing stolen data when victims dont pay the ransom demand. The number of infected users is rising. The REvil also known as Sodinokibi ransomware was first identified on April 17 2019.
Sodinokibi REvil Virus - Sodinokibi REvil Ransomware. Its routines configuration and behavior what weve come to expect from a mature family thats obviously well used in the criminal underground. Uncensored Interview with REvil Sodinokibi Ransomware.
This is an unedited interview which was originally released on October 23 2020 by the Russian OSINT on their YouTube channel. REvil aka Sodinokibi Clop and Conti. Sodinokibi sometimes also called REvil is ransomware-type malware - it encrypts files on infected machines and demands a ransom from the victims to restore the files.
31 Zeilen REvil is a ransomware family that has been linked to the GOLD SOUTHFIELD group and operated as ransomware-as-a-service RaaS since at least April 2019. Prominentestes Opfer der Ransomware war das internationale Finanzunternehmen Travelex das über Silvester angegriffen wurdeAnfang des Jahres gab die dafür verantwortliche Hacker-Gruppe an im Besitz von mehr als 5 GB sensibler Daten zu sein darunter Sozialversicherungsnummern Geburtstagen und natürlich Bankkartendaten. Uses random 6-character extensions.
The operators of the REvil Ransomware otherwise known as Sodinokibi have announced that they will use stolen files and data as.

Revil Ransomware Attack Windows Users Via Rdp Servers Exploit Kits Computer Security New Tricks Server

Jedes Zweite Unternehmen Muss 2019 Seine Windows Version Aktualisieren Auf 56 Prozent Der Desktop Arbeitsplatze In Kleinen Firmen Muss In Diesem Jahr Die Windo

Revil S Ransomware Success Formula Constant Innovation

Revil Revealed Tracking A Ransomware Negotiation And Payment
Revil Sodinokibi Ransomware Information

Mcafee Atr Analyzes Sodinokibi Aka Revil Ransomware As A Service What The Code Tells Us Mcafee Blogs

Emotet Uses Camouflaged Malicious Macros To Avoid Antivirus Detection A New Emotet Trojan Variant Has Been Observed I Malicious Detection Wireless Networking

Revil Ransomware Angriff Auf Kaseya Vsa Was Sie Wissen Sollten
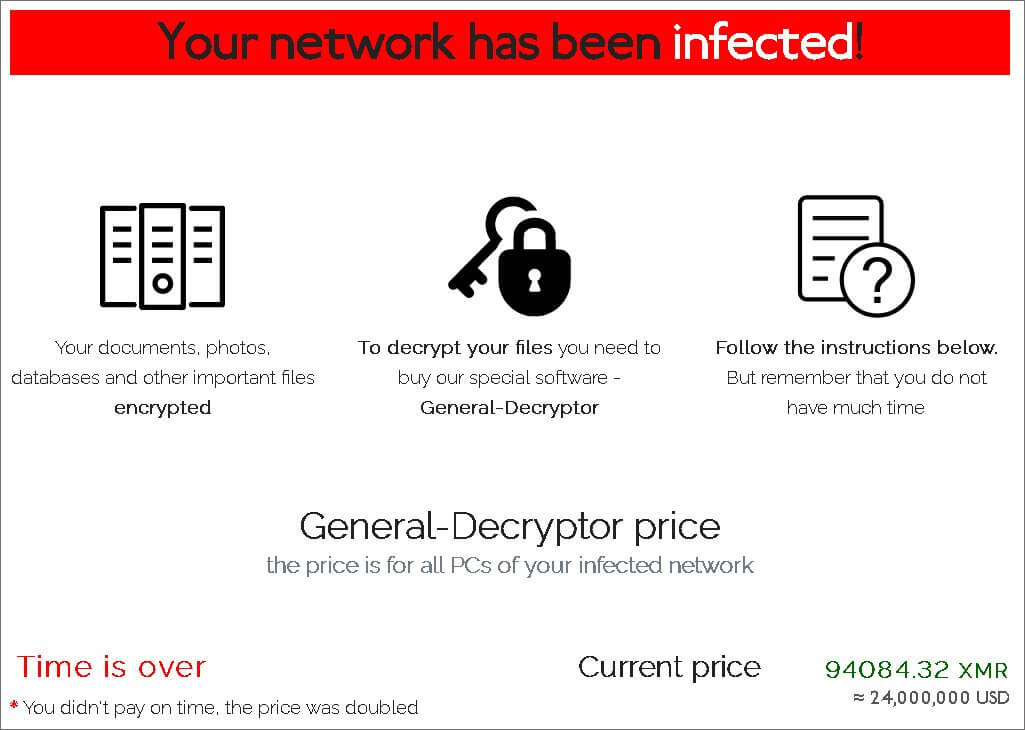
Asteelflash Releases First Statements Following Revil Ransomware Attack

Blog Updates Of Ethical Hacking Cyber Security Icss Cyber Security Awareness Cyber Security Digital Marketing Tools

Cyber Security News For 11may2020 Cyber Security Security Ipv6

Taking Deep Dive Into Sodinokibi Ransomware Acronis Com

Computer Security Info Protects System From External Threat Computer Security System Restore Antivirus Program

Sophos Analysiert Ransomware As A Service Revil

Ransomware Versteckt Sich Hinter Bewerbungen Bewerbung Personalabteilung Die Macher

Is Revil The New Gandcrab Ransomware In 2021 Extortion Tech Blogs Farewell Message

Revil Sodinokibi Ransomware Secureworks In 2021 Notes Template Lower Case Letters Ransom

Cyber Security News For 8may2020 Cyber Security Digital Ocean Security
